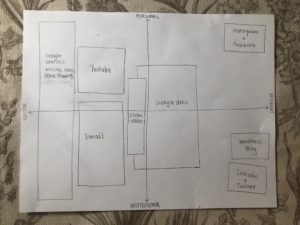
My VR Map
What digital platforms are students currently using to develop their professional network?
I believe the biggest digital platform at the moment that students are using to develop their professional network is LinkedIn. LinkedIn is the largest professional networking site today and is a great platform to promote yourself and the skills you can bring to a job. I first heard about LinkedIn when I was on my first co-op at Interior Health. My supervisor recommended I create a profile in order to document my skills, educational background, and work experience. Ever since then, I am constantly on the app or website scrolling through so many amazing peoples post that inspire me to achieve my professional goals someday. Another digital platform that students are utilizing is Twitter. Twitter allows individuals to follow other people in their field and by commenting on their tweets or even retweeting, it can significantly increase ones digital profile for recruiters.
What could the student consider to expand their professional learning network?
Some tips that can be applied for further expanding your professional learning network on Twitter is by following headhunters, internal recruiters, and hiring managers. Twello.com can be used to start making connections as it allows you to search by keyword, category, or both (Fletcher, 2019). Another tip is to retweet strategically because a majority of the people you retweet will notice, which increases the likelihood that they will pay more attention to you for cool opportunities (2019). Lastly, writing a strong bio can be of great help (2019). The best Twitter bios combine personal information and professional details with a confident tone. In addition, Twitter bios also allow you to link other digital platforms such as LinkedIn (2019).
How does data privacy and security limit and/or promote a PLN?
Data privacy and security are very important aspects to acknowledge when using digital platforms. Several attacks are introduced with personal learning networks, including data mining, phishing attempts, malware sharing, and botnet attacks (Tulane, n.d.). Data mining occurs every time someone creates a new social media account because they provide personal information that is stored and leveraged by companies to better target advertising to users (n.d.). Phishing is found to be the most common way to gain access to sensitive personal information through sending messages that look legitimate from organizations (n.d.). Malware sharing is utilized for gaining access to computers in order to retrieve certain data such as personal information, extort money, etc (n.d.). Botnet attacks are used to steal data, send spam, and launch distributed denial-of-service (DDoS) attacks in order to leverage cybercriminal access (n.d.).
In your network how can you create a digital identity/reputation?
Nowadays, it is super quick and easy to create a digital identity at any time and any place. There are some useful steps that you can take to develop a thoughtful digital presence (Bogle, 2019). First, it is important to identify what your main goal/accomplishment is for creating a digital identity (2019). It can be as simple as sharing your writing on a widely-read platform or connecting like-minded individuals (2019). Secondly, decide which digital platform you what to utilize for your presence. Thirdly, determine what type of content you want to publish to the world (2019). Lastly, brainstorm and develop a short and sweet personal brand statement or personal mission statement that conveys and guides the content you will publish (2019). Remember to make it authentic!
Find out what a local employer would do if you applied for a job with them?
The first thing an employer would do is browse through my cover letter and resume to see if I would be a good match for the position and highlight any skills/qualifications that stand out and pertain to the job. Since I have my PLN (LinkedIn) attached at the top of my resume, they may search it up out of curiosity or if needed. They may call my references that I have attached to my resume in order to further gain insight on what kind of person/employee I am. Lastly, if I am qualified and a good fit, the employer would contact me via phone or email to set up an interview time and day!
References:
Bogle, J. (2019). How to Create a Digital Identity Beyond Branding. Idealist. Retrieved from https://www.idealist.org/en/careers/create-digital-identity-branding
Fletcher, L. (2019). 11 concrete ways to use Twitter for networking. Blue sky BLOG. Retrieved from https://www.blueskyresumes.com/blog/11-concrete-ways-to-use-twitter-for-networking/
Tualne. (n.d.). Key Social Media Privacy Issues for 2020. Retrieved from https://sopa.tulane.edu/blog/key-social-media-privacy-issues-2020
